What is iMessage Contact Key Verification, and how to enable it on iPhone?
Protect your iMessage conversations with Contact Key Verification.
Imagine sharing personal moments or discussing sensitive information over iMessage, all while wondering, “Is this conversation really secure?” To make your digital chats end-to-end encrypted, Apple offers iMessage Contact Key Verification. This feature adds an extra layer of protection from prying eyes. Let’s learn what this feature is, how it works, and how to turn on iMessage Contact Key Verification on an iPhone.
What is iMessage Contact Key Verification?
After Advanced Data Protection, iMessage Contact Key Verification is Apple’s latest privacy feature. It allows users to check if the person they’re talking to is the intended recipient, not an attacker impersonating that person.
Contact Key Verification creates a unique code for your Apple ID, stored on Apple servers. When you message someone with this feature, iMessage checks their code from servers to ensure the message reaches the right person.
So, it provides an extra layer of security for users such as journalists, human rights activists, and government officials who are at a higher risk of facing sophisticated cyberattacks. Only the sender and recipient – not even Apple – can read the messages thanks to the end-to-end encryption.
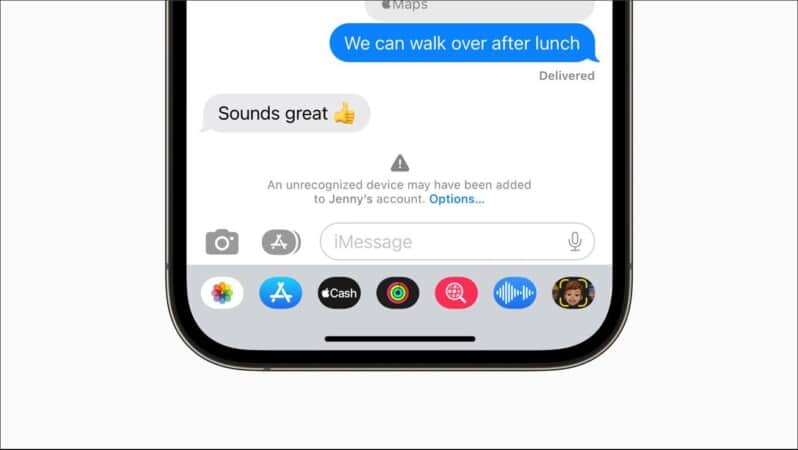
Contact Key Verification uses Key Transparency to automatically verify the codes in the background.
- iMessage lets you validate the identity of the contacts saved on your iPhone. You can’t verify unknown numbers.
- If a user has Contact Key Verification enabled, and the keys don’t match, they’ll be notified about such discrepancies in the Messages conversation and Apple ID Settings.
- Users with this feature enabled on their devices can compare a Contact Verification Code in person, via FaceTime, or another secure call. Once validated, they can update the contact information with the latest key.
- Once you turn on the feature, it will be applied to all of your devices logged into your Apple Account. If you own any outdated devices, you can still keep using them, but you’ll need to sign out of iMessage on these devices before enabling the feature.
Requirements to use iMessage Contact Key Verification
Your iPhone or iPad must have the following to enable iMessage Contact Key Verification:
- All devices should be updated to iOS 17.2 or later and iPadOS 17.2.
- Use the same Apple ID to sign into iCloud and iMessage across your devices.
- Enable iCloud Keychain and two-factor authentication for every Apple device.
- Set a password or passcode on your devices.
- Ensure you don’t use a managed Apple account.
How to turn on iMessage Contact Key Verification on iPhone
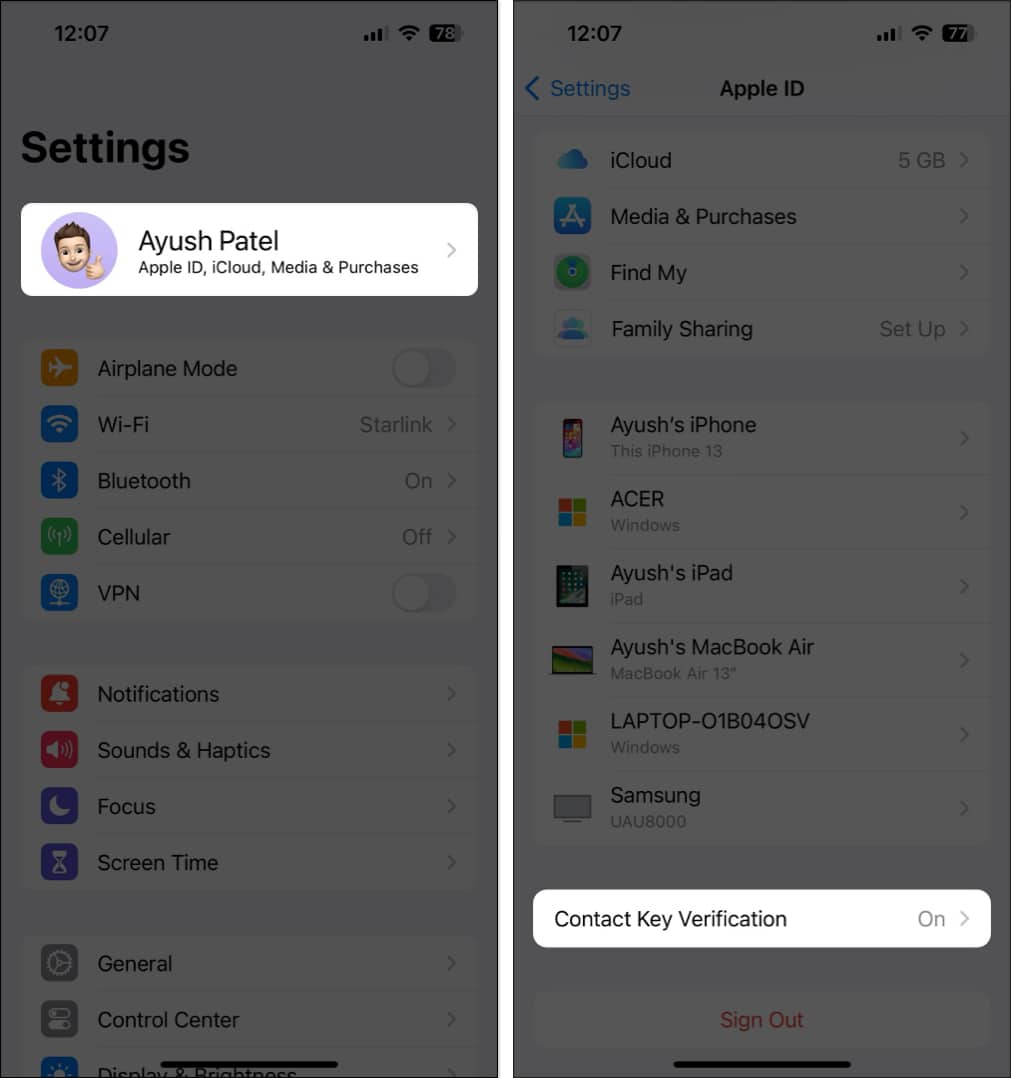
- Open the Settings app on your iPhone.
- Tap the Apple ID banner with your name.
- Scroll down and tap Contact Key Verification.
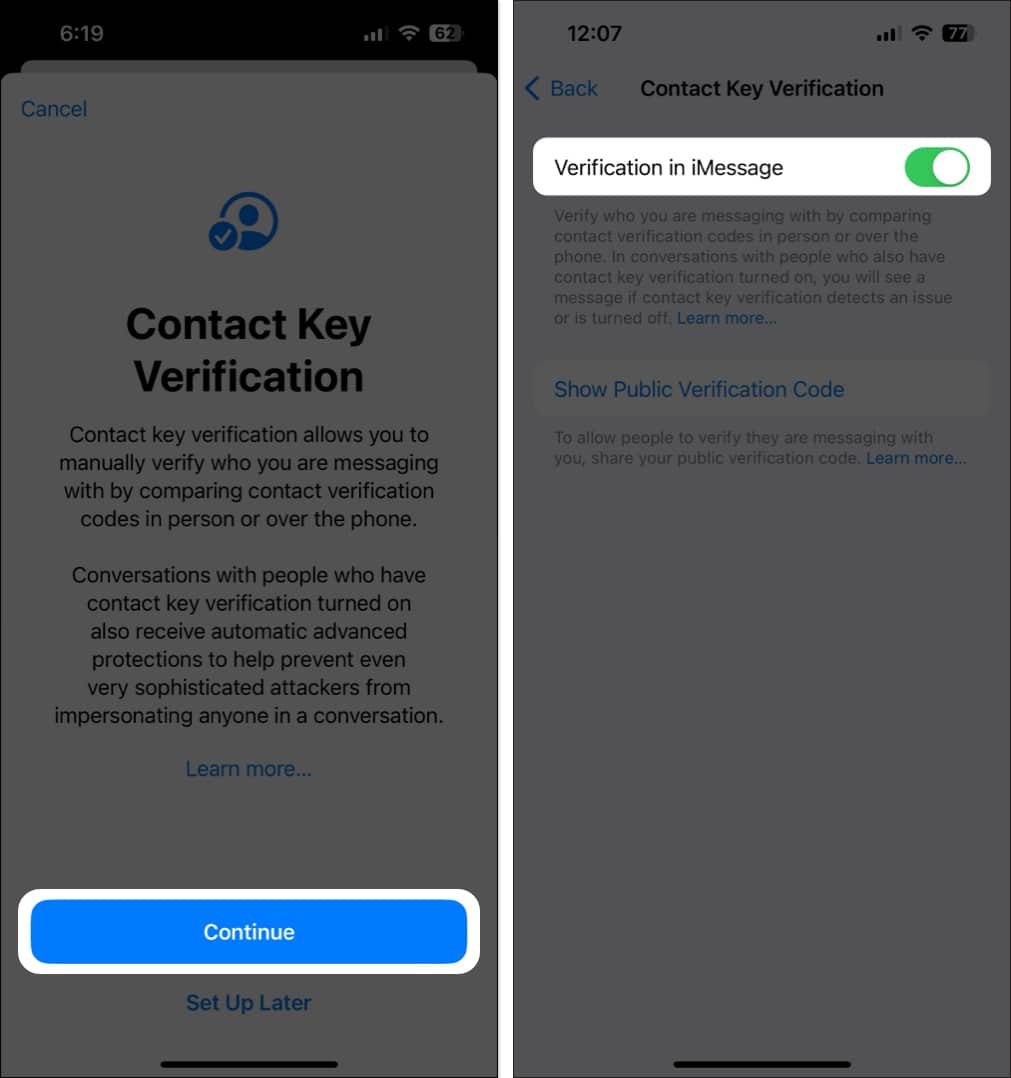
- Tap Continue → Toggle on Verification in iMessage.
Now, whenever iMessage detects an issue while validating the contact keys, it will notify you about it. If an unrecognized device logs into the recipient’s Apple ID or the contact turns off the feature, iMessage will alert you. To be sure, you can check the verification status and validate it manually.
Check iMessage Contact Key Verification status
Whenever I intend to share any sensitive information via iMessage, I first check if the contact is verified.
- Go to Messages and open an existing chat, or tap the pen icon to start a new conversation.
- In the thread, tap on the contact’s name at the top.
- Scroll down, and you will see the verification status.
- It will show Verification Off if the contact hasn’t enabled the feature. You may ask them to opt-in.
- If you see a Verify Contact option, this means, you need to validate the person’s identity.
- There will be a checkmark beside the contact’s name if it’s already verified.
- If iMessage has a validation issue, you will see an alert.
Based on the status, you can take action. If verification is pending or there is an issue, you must manually check the contact’s identity. Let me share how to do that.
Manually verify contacts on your iPhone
You may manually validate contacts if you want to be extra sure you’re texting the right person. First, save the contact and then follow the steps to manually check.
Method 1: On-device comparison
This process should be performed by both the sender and receiver on their devices at the same time.
- Connect to a reliable internet connection.
- Open the Messages app and tap on the contact’s name.
- Tap the Verify Contact option at the bottom. When both parties tap it, a six-digit code will be generated and displayed.
- Now, you can validate this code in-person or on a secure call.
Once you validate the code, press Mark as Verified to save the new key to that person’s Contact Card. If the codes don’t match, select No Match. This means you may not be chatting with the intended recipient. I advise you not to message the contact until you verify it.
Though the method is useful, I find it a bit inconvenient as both parties need to follow the steps simultaneously. That’s why I prefer using the next method to verify Contact Keys.
Method 2: Via Public Verification Code
IMessage lets you generate a Public Verification Code for your contact. As this code doesn’t contain any personal details, you can share it with anyone. Thus, they can quickly confirm your identity. Additionally, you may confirm by using other people’s public verification codes. To generate the code:
- Open Settings and go to your Apple ID.
- Tap Contact Key Verification and select Show Public Verification Code.
- It will display an alphanumeric code. Tap Copy Verification Code to save it in your clipboard.
- Hit OK to continue. Now, you can share the code anywhere by pasting it.
If you have other’s public verification code, you can use it to validate their contact by following these steps:
- Go to the Contacts app and open their contact.
- Tap Edit at the top right corner.
- Scroll down and select add verification code.
- Now, paste the verification code.
If it matches with the key stored in Apple servers, you will see a checkmark next to the contact’s name. However, if the checkmark doesn’t appear, you may ask them to verify contact using the first method.
Wrapping up…
Contact Key Verification makes it easy for iPhone users to ensure that their conversations are private and reach the right person. You don’t have to worry about the government, hackers, and other bad actors intercepting them. However, be aware of the fishing and text-based scams as this feature doesn’t alert you about these.
Will you be using it on your device? Let us know in the comments section below.
FAQs
Yes, it’s safe to share your Public Verification Code on social media or other platforms, as this doesn’t contain any private information. However, you should only share your Verification Code in person or via a secure voice/FaceTime call.
Contact Key Verification is better than traditional end-to-end encryption as it adds an additional layer of security by verifying the identity of the person you’re chatting with. So, it prevents attackers from impersonating someone you know and gaining access to your private conversations.
Also read: